Researchers study users to increase cyber security
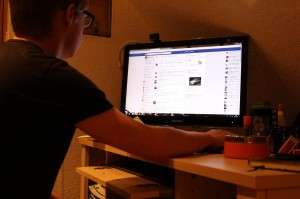
Missouri University of Science and Technology researchers are working to build a framework to study the online behavior of Internet users and how that behavior affects the safety of systems and networks.
Dr. Maggie Cheng, associate professor of computer science at Missouri S&T, and Dr. Fiona Nah, professor of business and information technology at Missouri S&T, are working with a two-year grant from the National Science Foundation. The researchers are looking to design experiments to study the characteristics of user behavior, Cheng says, creating a theoretical framework to study human cyber behavior.
Computer systems can be vulnerable because of unexpected human behavior, Cheng says, including situational behavior. "We're trying to consider in what ways user behavior can change the network state," she says.
Network users are not always conscious of risks and aware of security issues. A user can unintentionally compromise a network's security, such as by opening a seemingly innocuous email that turns out to be a virus that infects a whole system. A user's psychological state and cognition capacity affect cyber behavior, and a user's situational cyber behavior also depends on the user's own assessment of the risk. For instance, a user may not want to click on a link received from an email when fully risk-conscious, but when the user is under time pressure or believes the link is what it appears to be, the user may still do it.
A user's cyber behavior may also vary with the network and device the user is on. Cheng says that a user most likely will be more conscious of risk on the networks and devices that have higher security requirements. Malware targeted at mobile devices, such as those found on fake game sites, can easily be downloaded and installed because of users' low security awareness.
"The psychology of a hacker is different from an IT person and an ordinary network user," Cheng says. "IT looks at how it can secure the network by improving security policies, but a hacker views the users-caused vulnerability as an opportunity to take what is gleaned and go from there."
Provided by Missouri University of Science and Technology